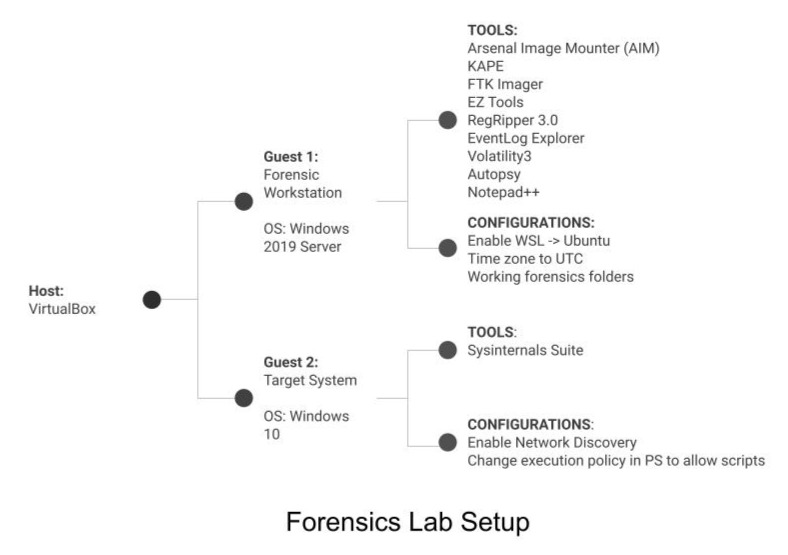
Windows Forensics Home Lab
- Configured a forensics workstation and target machine, executing scripts to simulate attacks.
- Acquired and analyzed memory dumps and disk images using AIM, KAPE, and FTK Imager. Investigated registry, file system, program execution, and logs with Zimmerman Tools and RegRipper.
- Performed memory forensics on dumps with Volatility3.